Cheat sheet for security+
Malware
- virus: need people action to execute and spread. Hoax: trick the victim to infect, like game.
- worms: spread and execute without humman
- trojans: can get remote control. RAT(remote access Trojan)
- ransomware: take control of your computer system, pay for unlock, most time will not unlock if you pay
- spyware: audit the callender, website history and other actions.
- rootkit: a type of backdoor, software design to administrative level control or root priviledge without detection.
- use DLL injection. malicious code inserted into a running process or kernel-mode device drvier. intercept calls and redirect to the malicous code.
- spam: CAN-Spam Act law to stop relaying send out email through other's mail server. Spim(instant message) like chat, text message.
- DaaS: Desktop as a Service provides a full virtualized desktop environment from within a cloud-based service. For example, play games shadow PC that is vitalized Win10 home gaming PC in the cloud.
- IaaS: just have the platform, install software by themselves.
- MSSP: A managed security service provider (MSSP) provides security as a service (SECaaS).
- QoS: Quality of service is the description or measurement of the overall performance of a service, such as a telephony or computer network or a cloud computing service, particularly the performance seen by the users of the network.
Stateless
It does not preserve information about network sessions. Each packet is analyzed independently, with no record of previously processed packets.
- HOTP: Event-based One-Time Password
- TOTP: Time-based One-Time Password
Retinal or iris scanning
retinal 视网膜扫描,recognize the blood vessel. influenced by the disease.
Iris scanning, 虹膜扫描, recognize the iris shape, simpler and hard to be influenced by disease.
North-south traffic, between data center and client
East-west traffic, in data center, server to server.
DMZ for some servers exposed publicly, like SMTP. DMZ and intranet have different subnet.
How DMZ implement: By using two firewalls (external and internal) around a screened subnet, or by using a triple-homed firewall (one with three network interfaces).
Extranet is for the supplier, partner, client.
Intranet is for employee, like HR to tech.
Routing protocols include BGP, Open Shortest Path First (OSPF), Enhanced Interior Gateway Routing Protocol (EIGRP), and Routing Information Protocol (RIP).
STP:Spanning tree protocol, in order to prevent router loop. It can reduce the loop node. Bridge Protocol Data Unit (BPDU) Guard will set the port as disable when it received the BPDU.
Load balancing
layer 4 : transmit packets with IP and port, LVS, F5
layer 7 : transmit packets with URL, Nginx, Apache.
Persistence is a layer 7 mechanism that works by injecting a session cookie. This is generally more reliable than the layer 4 source IP affinity mechanism.
SIEM(security information and events management): products aggregate IDS alerts and host logs from multiple sources, then perform correlation analysis. In addition to logs from Windows and Linux-based hosts, this could include switches, routers, firewalls, IDS sensors, vulnerability scanners, malware scanners, data loss prevention (DLP) systems, and databases.
- Install agent on each host
- syslog with SNMP to collect
- sensor to sniff packets
DNS
- DHCP server can dynamically allocate IP, gateway, DNS, so rogue DHCP server may cause DOS(direct to an invalid IP address) or to malicious address.
- Hosts file will influence DNS or not? Probably. The contents of the HOSTS file are written to the DNS cache on startup. It is possible to edit the registry to prioritize DNS over HOSTS, though.
LDAP:
Use TLS to encrypt data, but for authentication is use plaintext, so it is not secure.
The Simple Authentication and Security Layer (SASL) allows a choice of authentication providers and encryption (sealing)/integrity (signing) mechanisms.
("CN=Dev-India,OU=Distribution Groups,DC=gp,DC=gl,DC=google,DC=com");CN = Common NameOU = Organizational UnitDC = Domain Component
SNMP:
Agents and monitor. Agents contain switch, router, server.This agent maintains a database called a management information base (MIB) that holds statistics relating to the activity of the device.
The SNMP monitor (a software program) provides a location from which network activity can be overseen.
- SNMP community names are sent in plaintext and so should not be transmitted over the network if there is any risk that they could be intercepted.
- Use difficult to guess community names; never leave the community name blank or set to the default.
- Use Access Control Lists to restrict management operations to known hosts (that is, restrict to one or two host IP addresses).
- SNMP v3 supports encryption and strong user-based authentication. Instead of community names, the agent is configured with a list of usernames and access permissions. When authentication is required, the SNMP message is signed with a hash of the user's passphrase. The agent can verify the signature and authenticate the user using its own record of the passphrase.
mail protocol:
pop3 download email from server, will not sychronize with the server and user's end. port 110
IMAP: can download mail from server, and can connect multiple device and sychronize with the user's action. port 143
SMTP: deliver mail and discover recipient SMTP server with using the domain name part of the email address. The SMTP server for the domain is registered in DNS using a Mail Exchanger (MX) record.
user send message use port 587,
mail send between servers use port 25
MIME:(for email) Multipurpose Internet Mail Extensions is an Internet standard that extends the format of email messages to support text in character sets other than ASCII, as well as attachments of audio, video, images, and application programs.
Use recepient's public key to encrypt message, so only recipient can dcrypt the message.
SIP(for VoIP): Session Initiation Protocol: for audio, vedio connection, based on UDP.like zoom meeting. port 5060 typically.
discover user, advertizing calls, negotiate sessions parameters in VoIP(Voice over IP).
After connection, use real-time Transport Protocol (RTP) to transport message.
SRTP(secure real time ransport protocol)ensure the confidentiality for the actual call data.
IPSec: prevent from man-in-the-middle and spoofing attacks in communications in VPN tunnel or normal communication. IPSec can provide both confidentiality (by encrypting data packets) and integrity/anti-replay (by signing each packet). The main drawback is that it adds overhead to data communications. IPSec can be used to secure communications on local networks and as a remote access protocol.
two protocols in IPSec:
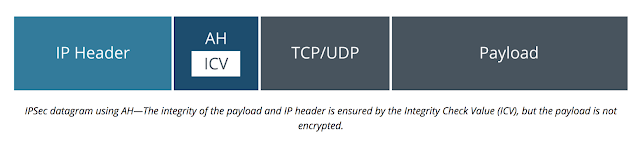
AH(Authentication Header): performs a cryptographic hash on the whole packet, including the IP header, plus a shared secret key (known only to the communicating hosts), and adds this HMAC in its header as an Integrity Check Value (ICV).
only ensure the integrity, not include confidentiality because payload is not encrypt.
method: encypt the whole packets and add an IP header to know the src IP and dest IP.
ESP(Encapsulation Security Payload):provides confidentiality and/or authentication and integrity. It exclude IP header and include payload to encrypt. Trailyer provide padding for the cryptographic function.AH VS ESP: both use HMAC-MD5 or HMAC-SHA, but cover different part.
The AH protocol provides a mechanism for authentication only. Because it doesn't encrypt payload and calculate the HMAC of header and the payload, AH authenticates IP headers and their payloads.
The ESP protocol provides data confidentiality (encryption) and authentication
IPSec can be used in two modes:
Transport mode—both AH and ESP. this mode is used to secure communications between hosts on a private network (an end-to-end implementation). When ESP is applied in transport mode, the IP header for each packet is not encrypted, just the payload data. If AH is used in transport mode, it can provide integrity for the IP header.
Tunnel mode—only ESP. this mode is used for communications between VPN gateways across an unsecure network (creating a VPN). This is also referred to as a router implementation. With ESP, the whole IP packet (header and payload) is encrypted and encapsulated as a datagram with a new IP header. AH has no real use case in tunnel mode, as confidentiality will usually be required.
Layer 2 Tunneling Protocol (L2TP) is used to conjunction with IPSec to provide a remote access client VPN with user authentication.
Some SSO method or protocols:
- SAML: based on XML. for authentication and authorization SSO and login in token without password. User agent send request to SP, if the user doesn't have valid session, SP redirect to IDP(identification provider), IDP sends the assertion to SP(service provider).
- Shibboleth is a web-based Single Sign-On infrastructure. It is based on SAML
- OAuth: only authorization not authentication, generate a token, not preserve password
- OpenID: extension of OAuth. OpenID connec(OIDC) is more suit for mobile apps.
Remote login
- TACACS+: (by Cisco) Terminal Access Controller Access Control System.
- Radius: Remote Authentication Dial-In User Service, is a networking protocol that operates on port 1812 and provides centralized Authentication, Authorization, and Accounting(AAA) management for users who connect and use a network service. Client is a device or server that accepts user connections, often referred to as a network access server (NAS) or as the authenticator. Using RADIUS architecture, the client does not need to be able to perform authentication itself; it performs pass-thru to an AAA server.
The client is not the user, client and server has a pre-shared key, the user send request and credential to the client, the client encrypt it with the pre-shared key and send it to the server, the server decrypt it and authenticate the user, then send to the client, the client authorize the user. The client can be access point, VPN gateway or switches.
- Kerberos: is an open-source network authentication protocol designed by Matte Challenge-Handshake Authentication Protocol (CHAP) is used to authenticate a user or network host to an authenticating entity.
TLS/SSL: X.509 standard
wireless standard: 802.1x:
- EAP(Extensible Authentication Protocol): like 802.1x relys on. It allows lots of different authentication methods, but many of them use a digital certificate on the server and/or client machines. This allows the machines to establish a trust relationship and create a secure tunnel to transmit the user authentication credential.
Encryption
- MD-5 creates a 128-bit fixed output.
- SHA-1 creates a 160-bit fixed output.
- SHA-2 creates a 256-bit fixed output.
- RIPEMD creates a 160-bit fixed output.
- NTLM creates a 128-bit fixed output.
Disk encryption
TPM: Trusted Platform Module is a hardware-based cryptographic processing component that is a part of the motherboard.
PAM: Pluggable Authentication Module is a device that looks like a USB thumb drive and is used as a software key in cryptography.
FDE: Full Disk Encryption can be hardware or software-based.
OS-ACL based is not secure because if an adversary can attach the drive to a different host OS. FDE can solve this probelm, but it can also reduce the performance. Then we have (SED)self-encrypting drives that the user password can be changed without having to decrypt and re-encrypt the drive.
Asymetric:
- PGP asymetric encryption algrithm, encrypt data with a ramdon key first and then encrypt it with the receiver's public key.
- RSA
- ECC
Symetric:
- twofish
- blowfish
- DES
- RC4
- AES
Data destruction or sanitization
Wiping: overwrite data many times, only reusable.
Shredding: physical destroy, cannot reuse.
degaussing: demagnetizing, cannot reuse.
Purging: cannot reuse(like degausser)
Evidence collection order:
Processor Cache, Random Access Memory, Swap File , and then the Hard Drive or USB Drive.
ping attacks
Ping flood: with botnet to attack.
Smurf attack: make use of router broadcast, relected attack.
Ping of death: length is higher than 65535, cause buffer overflow.
ACL VS NAC
NAC(network access control): is an approach to attempts to unify endpoint security technology (such as anti-virus, host intrusion prevention, and vulnerability assessment), the user or system authentication, and network security enforcement. When a remote workstation connects to the network, NAC will place it into a segmented portion of the network (sandbox), scan it for malware and validate its security controls, and then based on the results of those scans, either connect it to the company’s networks or place the workstation into a separate quarantined portion of the network for further remediation.
can monitor unauthorized user which is attempting to connect VPN.
ACL: is a type of network traffic filter that can control incoming or outgoing traffic.
Non-credentialed scans VS Credentialed scans
Credentialed scans log into a system and retrieve their configuration information. Therefore, it should provide you with the best results.
Non-credentialed scans rely on external resources for configuration settings that can be altered or incorrect.
Security Through Obscurity (STO): nobody outside of its implementation group is allowed to find out anything about its internal mechanisms.
Bring Your Own Device (BYOD) and Choose Your Own Device (CYOD).
Q1:Your log shows that the Notepad process on a workstation running as the local administrator account has started an unknown process on an application server running as the SYSTEM account. What type of attack(s) are represented in this intrusion event?
The Notepad process has been compromised, possibly using buffer overflow or a DLL/process injection attack. The threat actor has then performed lateral movement and privilege escalation, gaining higher privileges through remote code execution on the application server.
Q2: how to detect a buffer-overflow?
Real-time detection of a buffer overflow is difficult, and is typically only achieved by security monitoring software (antivirus, endpoint detection and response, or user and entity behavior analytics) or by observing the host closely within a sandbox. An unsuccessful attempt is likely to cause the process to crash with an error message. If the attempt is successful, the process is likely to show anomalous behavior, such as starting another process, opening network connections or writing to AutoRun keys in the registry. These indicators can be recorded using logging and system monitoring tools.
memory leak:
A process claims memory locations but never releases them, reducing the amount of memory available to other processes. This will damage performance, could prevent other processes from starting, and if left unchecked could crash the OS.
DLL injection:
Various OS system functions allow one process to manipulate another and force it to load a dynamic link library (DLL). This means that the malware code can be migrated from one process to another, evading detection. .exe file invoke dll files, may invoke malicious dll files.
NTLM(NT LAN Manager): for integrity or confidentiality with 160-bit encryption. Many windows server use this anthenticate method, attacker can implement PtH(pass the hash) to get the hash of the credential to pass the authentication on the server.
But most server using kerberos(tickets) now, so this problems can be mitigated.
%3C and %3E are < and >
replay attack work in the context of session hijacking
The attacker captures some data, such as a cookie, used to log on or start a session legitimately. The attacker then resends the captured data to re-enable the connection.
clickjacking attack
The attacker inserts an invisible layer into a trusted web page that can intercept or redirect input without the user realizing.
persistent XSS attack
Where the attacker inserts malicious code into the back-end database used to serve content to the trusted site.
against XSS:
- output encoding.
- Filter input on arrival.
- Use appropriate response headers
- Content Security Policy
check the input vulneravilities: fuzzer.
How might an attacker exploit a web application to perform a shell injection attack?
The attacker needs to find a vulnerable input method, such as a form control or URL or script parser, that will allow the execution of OS shell commands.
You are improving back-end database security to ensure that requests deriving from front-end web servers are authenticated. What general class of attack is this designed to mitigate?
Server-side request forgery (SSRF) causes a public server to make an arbitrary request to a back-end server. This is made much harder if the threat actor has to defeat an authentication or authorization mechanism between the web server and the database server.
SSRF mitigation: whielist, limit port or intranet's IP. Unify the error message to prevent the attacker to exploit.
SSL striping:
A Secure Sockets Layer (SSL) strip attack is launched against clients on a local network as they try to make connections to websites. The threat actor must first perform a Man-in-the-Middle attack via ARP poisoning to masquerade as the default gateway.
senerio1: When a client requests an HTTP site that redirects to an HTTPS site in an unsafe way, the sslstrip utility proxies the request and response, serving the client the HTTP site, hopefully with an unencrypted login form. If the user enters credentials, they will be captured by the threat actor.
Sites can use the HTTP Strict Transport Security (HSTS) lists maintained by browsers to prevent clients requesting HTTP in the first place. Force the browser to send HTTPS request.
senerio2: When client connect to public WIFI, Krack attack in WPA2, reinstall the key, the key will be all zero, then implement the MitM attack, attacker to client is HTTP connection, attacker to the server is HTTPS connection.
Cloud:
public cloud: use 3rd party's hardware, like common AWS
private cloud: hardware is owned by the company, but may use cloud service, like AWS, more expensive and more secure
hybrid cloud: both have public cloud and private cloud.
community cloud: shared with other company.
bare metal: combine the cloud attribute and hardware attribute. A cloud machine with no OS installed.
CASB(cloud access security broker, KAZ-B): between the cloud provider and customer, used to audit the cloud policy and security.
A Virtual Desktop Environment (VDE) is the workspace presented when accessing an instance in a virtual desktop infrastructure (VDI) solution. VDI is the whole solution (host server and virtualization platform, connection protocols, connection/session broker, and client access devices).
SOA(Service-Oriented Architecture)
make use of loose couple, split the service into multiple components.
Microservices
similar to SOA, but decoupled.
SOA allows a service to be built from other services. By contrast, each microservice should be capable of being developed, tested, and deployed independently. The microservices are said to be highly decoupled rather than just loosely decoupled.
SDV:
Software-defined visibility (SDV) gives API-based access to network infrastructure and hosts so that configuration and state data can be reported in near real time. This facilitates greater automation in models and technologies such as zero trust, inspection of east/west data center traffic, and use of security orchestration and automated response (SOAR) tools.
SOAR 的全称是 Security Orchestration, Automation and Response,意即安全编排自动化与响应。
incident response is too complex to be wholly automated. SOAR assists the provision of runbooks, which orchestrates the sequence of response and automate parts of it, but still requires decision-making from a human responder.
Chef and Puppet: for DevOps
These are orchestration tools. Orchestration facilitates "automation of automation," ensuring that scripts and API calls are made in the right order and at the right time to support an overall workflow.
DLP is a generic term that may include data at rest, data in transit, or data in use to function.
block the transfer of tagged content over unauthorized channels.
MDM(Mobile device Management) is the process of managing all the contents of a mobile device. MDM includes storing basic information about a mobile device, determining what applications can exist on the device, locating the device, and protecting the device if it is lost or stolen
network tap: 网络分流器,它直接插入到网络电缆和发送一份网络通信给其它设备。passive收集流量进行分析, it used for IPS/IDS.
port mirror: set another port to collect packets passively, similar to network tap. But it cannot copy all the packets and may have some delay.
SNMP is used to monitor network devices but is considered active monitoring
forencis order:
sets out the general order as follows:
1.CPU registers and cache memory (including cache on disk controllers, GPUs, and so on).
2.Contents of nonpersistent system memory (RAM), including routing table, ARP cache, process table, kernel statistics.
3.Data on persistent mass storage devices (HDDs, SSDs, and flash memory devices):
- Partition and file system blocks, slack space, and free space.
- System memory caches, such as swap space/virtual memory and hibernation files.
- Temporary file caches, such as the browser cache.
- User, application, and OS files and directories.
4.Remote logging and monitoring data.
5.Physical configuration and network topology.
6.Archival media and printed documents.
EnCase (for Windows memeory)Forensic is a digital forensics case management product. Case management is assisted by built-in pathways, or workflow templates, showing the key steps in diverse types investigation. In addition to the core forensics suite, there are separate products for e-discovery (digital evidence management) and Endpoint Investigator (for over the network analysis of corporate desktops and servers).
The Forensic Toolkit (FTK) from AccessData is another commercial investigation suite designed to run on Windows Server (or server cluster).
The Sleuth Kit is an open-source collection of command line tools and programming libraries for disk imaging and file analysis. Autopsy is a graphical front-end for these tools and acts as a case management/workflow tool. The program can be extended with plug-ins for various analysis functions. Autopsy is available for Windows and can be compiled from the source code to run on Linux.
WinHex from X-Ways is a commercial tool for forensic recovery and analysis of binary data, with support for a range of file systems and memory dump types (depending on version).
The Volatility Framework is widely used for system memory analysis.
dd if=/dev/sda of=/mnt/usbstick/backup.img
dd command to make a copy of an input file (if=) to an output file (of=) and apply optional conversions to the file data.
forencis source and method:
- Network: most from SIEM
- Cache: can refer either to hardware components or software. file system and disk image. For example, each brower has a cache of temporary files. Some cache artifacts generated by the OS and applications are held in memory only, such as portions of the registry, cryptographic keys, password hashes, some types of cookies, and so on. The contents of hardware cache (CPU registers and disk controller read/write cache, for instance) is not generally recoverable.
- Snapshot: from virtual machine or cloud process.
- Firmware: often for flash memory. extract from OS
Q1:create forensic disk images without making changes to the original evidence:
FTK imager(for windows)
Q2: What type of forensic data is recovered using a carving tool?
A carving tool allows close inspection of an image to locate artifacts. Artifacts are data objects and structures that are not obvious from examination by ordinary file browsing tools, such as alternate data streams, cache entries, and deleted file remnants.
用来采证分析已经被删除或者被隐藏的文件。如autospy.
The Memdump, Volatility framework, DumpIt, and EnCase are examples of Windows memory capture tools for forensic use. The dd tool is used to conduct forensic disk images. Wireshark is used for packet capture and analysis. Nessus is a commonly used vulnerability scanner.
service level agreement(SLA)
The data steward role is concerned with the quality of data (format, labeling, normalization, and so on). The data custodian role focuses on the system hosting the data assets and its access control mechanisms.
data confidential range: public, confidential/secret, or critical/top secret
- Data minimization: when retrieve data, need to state where to use this data, how long will use.
- Anonymization(匿名化):don't know who has these imformation.
- Pseudo-anonymization(假名化): sensitive information can be replaced by other data, and can reverse back the original data. eg: Alice, 20 year-old change to 00532, 20 year-old, this code can reverse to Alice.
- Data masking(数据脱敏): replace with x, like input password.
- Aggregation/Banding: change the accurate data to range, like 25 to 20-30.
- Tokenization—replacing data with a randomly-generated token from a separate token server or vault. This allows reconstruction of the original data if combined with the token vault.
- Data correlation: 让sensor根据相关性收集相关数据
PII: personal identification data, 用户private信息, 如电话家庭住址等
SPI: sensitive personal data, 种族等
PHI:用户健康保险等信息
- DAC :Discretionary access control 任意权限控制。文件所有者可以修改文件的ACL
- RBAC :Role-based access control (基于角色的访问控制):管理员赋予一系列角色。
- ABAC :Attribute-based access control (基于属性的访问控制):Attribute-based access control (ABAC) provides the most detailed and explicit type of access control over a resource because it is capable of making access decisions based on a combination of subject and object attributes, as well as context-sensitive or system-wide attributes
- MAC: Mandatory Access Control(MAC):strongest level of protection.管理员管理访问控制。如管理员的访问级别65535,Alice的是100,客人(Guest)是1,有两个文件,file1级别2,file2级别200,这样Alice只能访问file1,客人不能访问file1和file2,管理员两个文件都可以访问。
agent-based scanning:
可以在脱机情况下扫描,当联网后发给server端。
incident response life cycle
Preparation, Identification, Containment, Eradication, Recovery, and Lessons Learned.
TTP: Tactics, Techniques, and Procedures
It is specified in MITRE's ATT&CK framework.
CIRT: Computer emergency response team
flow records only collect metadata and statistics, not every frame.
Flow records are generated by NetFlow or IP Flow Information Export (IPFIX) probes. A flow record is data that matches a flow record, which is a particular combination of keys (IP endpoints and protocol/port types).
out of band: 带外管理:存储设备的管理控制数据与用户业务数据信息在不同的链路传送,即管理一条线,业务一条线。
Why out of band? The response team needs a secure channel to communicate over without alerting the threat actor. There may also be availability issues with the main communication network, if it has been affected by the incident.
in band: 带内管理:存储设备的管理控制数据与用户业务数据信息在相同的链路传送,即管理和业务同一条线。
Q1: You take an incident report from a user trying to access a REPORT.docx file on a SharePoint site. The file has been replaced by a REPORT.docx.QUARANTINE.txt file containing a policy violation notice. What is the most likely cause?
This is typical of a data loss prevention (DLP) policy replacing a file involved in a policy violation with a tombstone file. It inlcude the policy violation and how to get back the original file, but not contains the oringinal contents.
RCA(Risk and Control Assessment):
Risk Types:
- External: disaster
- internel: assets and workflows
- Multiparty:adverse event impacts multiple organizations. Multiparty risk usually arises from supplier relationships. eg: ISP, cloud these kind of 3rd party service you use on your orgnization.
- Intellectual Property (IP) Theft(知识产权盗窃): data of commercial value that is owned by the organization.
- Software Compliance/Licensing: install software without buying
- Legacy Systems: example: product which no longer receive security updates. windows XP
Single Loss Expectancy (SLE)—The amount that would be lost in a single occurrence of the risk factor. This is determined by multiplying the value of the asset by an Exposure Factor (EF). EF is the percentage of the asset value that would be lost.
Annualized Loss Expectancy (ALE)—The amount that would be lost over the course of a year. This is determined by multiplying the SLE by the Annualized Rate of Occurrence (ARO).
Risk appetite is a strategic assessment of what level of residual risk is tolerable
Risk register: A document highlighting the results of risk assessments in an easily comprehensible format
control risk: the risk that may ineffectively mitigate the impact or likelihood of risk.
mission essential function (MEF): most critical thing
Maximum tolerable downtime (MTD)
Work Recovery Time (WRT):服务器恢复后,其他调整工作到恢复如初的时间。
Recovery time objective (RTO) :服务器(objective)恢复的时间。(服务器在恢复期间要测试Test,所以中间是T)
RTO+WRT 是修复服务器并调好配置的总时间,这个时候可以运行业务了 must not exceed MTD!
Recovery Point Objective (RPO) is the amount of data loss that a system can sustain, measured in time. 从业务被入侵导服务器恢复这段时间丢失导数据。(中间有个P,所以和人有关,是data)
single points of failure (SPoF):会影响resilience,因为是单服务器运作,没有备机。
Mean time to failure (MTTF):平均故障时长,通常是不可修复的
mean time between failures (MTBF):平均故障间隔时间,通常是换硬件,可修复的。
Full-scale or functional exercises:演习
power supply units (PSUs)
Disk redundancy:
RAID level 0: no back up, one break, whole break
RAID level 1: write to two disks, performance 50%
RAID level 5: more than 3 disks, This allows the volume to continue if one disk is lost.
RAID level 6:allows the volume to continue when two devices have been lost.
Nested: (0+1, 1+0, or 5+0)
Backup type:
- full: one tape, all files
- diffrential-based: backup new or modified files from the last full backup, so the b1<b2<b3
- incremental-based: backup new or modified files from last backup, b1=b2=b3
Online versus Offline Backups:
online is faster to restore data
Offiline is more secure
Q1.You are advising a company about backup requirements for a few dozen application servers hosting tens of terabytes of data. The company requires online availability of short-term backups, plus offsite security media and long-term archive storage. The company cannot use a cloud solution. What type of on-premises storage solution is best suited to the requirement?
The offsite and archive requirements are best met by a tape solution, but the online requirement may need a RAID array, depending on speed. The requirement is probably not large enough to demand a storage area network (SAN), but could be provisioned as part of one.
restore order:
In very general terms, the order of restoration will be as follows:
- Enable and test power delivery systems (grid power, power distribution units (PDUs), UPS, secondary generators, and so on).通电
- Enable and test switch infrastructure, then routing appliances and systems.通网
- Enable and test network security appliances (firewalls, IDS, proxies). 防火墙
- Enable and test critical network servers (DHCP, DNS, NTP, and directory services). 网络基础
- Enable and test back-end and middleware (databases and business logic). Verify data integrity. 后端
- Enable and test front-end applications.前端
- Enable client workstations and devices and client browser access. 让用户使用
juice-jacking: USB充电引起的data盗窃或攻击,mitigation: USB-data-blocker
HVAC:空调设备
preventing any type of unauthorized computing, network, or storage connection to a protected host?
air gap or secure area demilitarized zone (DMZ).
What physical security device could you use to ensure the safety of onsite backup tapes?
A fireproof safe or vault(保险库).
The Crossover Error Rate (CER) describes the point where the False Reject Rate (FRR) and False Accept Rate (FAR) are equal. CER is also known as the Equal Error Rate (EER). The Crossover Error Rate describes the overall accuracy of a biometric system.
NDA(Non-disclosure agreement )(保密协议): legal basis for protecting information assets.
(SLA)Service-level agreement (服务级别协议): between service provider and client
(MOU)Memorandum of understanding (备忘录): between two parties
ISA( interconnection security agreement): gover federal agency and a third party interconnecting their systems.
acceptable use policy (AUP) : for employee and employer
Be careful with NOT
The first mitigate thing means choose the highest level severity vulnerability.
At the end of your ACL rules, place implicit deny statements.
Same key words always show in problem and answer.
find the key word in the problem, like sigle->multiple. same word or opposite word.
When some words appear, like weak, slow, that's the problem we should fix.